Compliance could be an obligations or a privilege. Obligation means the basic requirements to meet, any short of which may subject you to punishment. Privilege means the extra benefits nice to have, any short of which could make you less competitive.
Classified protection (“CP”) is an obligation and a privilege under China’s Cybersecurity Law (“CSL”). If certified under CP, a company would have prima facie evidence that its network system meets some basic safety obligations under the CSL. The loopholes that are ever red-flagged could be then plugged up. With the obligations satisfied, the company could fend off some possible investigations or punishments resulting from the loopholes in cybersecurity.
How is CP conducted?
Under CP, network systems are graded from Level 1 to Level 5. The higher the level is, the more requirements to comply. The certification entities (which need certification licenses) would do testing and decide which level a network system is at, and advise where are vulnerabilities. However, a certification entity is not allowed to provide rectification services just like a referee cannot be a player simultaneously – the rectification services will have to be provided by rectification entities so as to tackle the vulnerabilities in IT, processes and control measures of the network system. Although a rectification entity does not need a license for its rectification services, the rectification entity has to have capacity in both IT and risk management.

Henry Chen received an award from National Information Security Standardization Technical Committee for his active and constructive participation in the drafting of national standards on cybersecurity and data governance
Why is CP important?
Simply, CP can help plug loopholes and tackle vulnerabilities in network systems. We may learn the importance of CP from the opposite cases below.
Case #1:
In February of 2018, Code repository GitHub was hit by a distributed denial of service (DDoS) attack which peaked at 1.35 Tbps via 126.9 million packets per second.

Henry Chen’s article Internet Spiders and Protection of Commercial Secrets received an excellent award from China Information Security Legal Conference
According to a statement the incident occurred on February 28 of 2018 and persisted for around nine minutes and originated from over a thousand different autonomous systems (ASNs) across tens of thousands of unique endpoints.
“The first portion of the attack peaked at 1.35 Tbps [between 17:21 and 17:30 UTC] and there was a second 400 Gbps spike a little after 18:00 UTC,” said Sam Kottler, manager of Site Reliability Engineering.
This attack registered even larger than the peak of the attack on Dyn in 2016, according to Wired.
By the end of February of 2018, there were 25,000 Memcached servers in China exposed on the Internet.
If the systems in China in use of Memcached servers had gone through CP under CSL, the incidents could have been most probably avoided.
Case #2:
In 2015, Fiat Chrysler issued a safety recall affecting 1.4 million vehicles in the US, after security researchers showed that one of its cars could be hacked. The hackers had taken control of a Jeep Cherokee via its internet-connected entertainment system. As a result, Chrysler issued a voluntary recall to update the software in affected vehicles.
From the cases above, you may realize that TP or similar risk management system is not just something nice to have. It is an insurance or a golden shield to manage risks and fend off liabilities.
CP is a compliance threshold for network safety. Different network systems may have some peculiar features. CP for a code repository like GitHub should be different from CP for autonomous driving in many dimensions, such as how to determine levels and how to deal with vulnerabilities. It is suggested to develop some CP guidance for some particular industrial sectors such as autonomous driving.
Is CP compulsory?
The answer is yes for any network operator – basically every business operator with network is a network operator no matter whether it is a critical information infrastructure operator (“CIIO”) or not. CSL provides for a compulsory CP test for a CIIO once a year.
CSL defines CIIO as the network system in the sectors of public telecommunication and information service, energy, communication, water resource, finance, public service and electronic public service. Once sabotaged, the CIIO could cause great and irreparable damages to itself and the entities around. China is drafting implementation rules for CSL to give a clear definition and description of CIIO.
CP is compulsory as well for non-CIIOs. If graded Level 3 or about, CP must be conducted at least once a year. Although many non-CIIOs did not undertake CP yet in spite of the legal requirements under the CSL, some did it to get the privilege for extra protection from being hacked and from being punished especially for those which rely on the Internet in delivery of products and services. It could be foreseen that law enforcement would be tightened on non-CIIOs when law enforcers are more experienced and implementations rules are more sophisticated and practical.
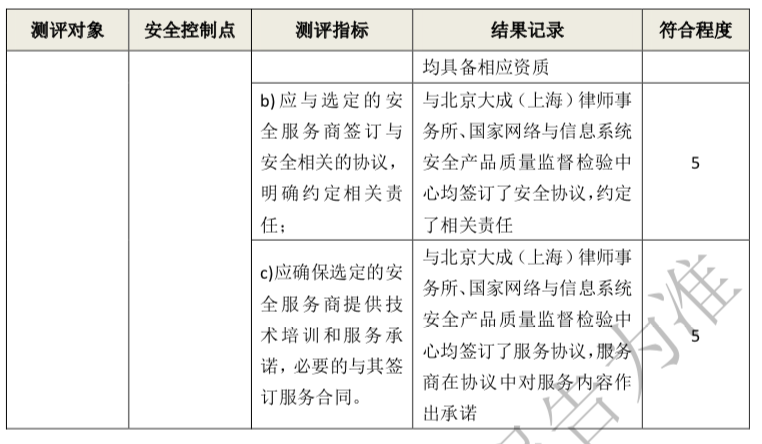
Dentons Shanghai Office was retained to provide classified protection services to a client
Case #3:
On July 22, 2017, the website of “teacher development platform” in Sichuan was hacked. Local cybersecurity department found that the website had not carried out CP compliance since launched – obviously, the cybersecurity department thinks that the hacking could have been stopped if the platform had adopted appropriate control measures. As such, the local authority issued the administrative punishment to the website operator with a fine of 10,000 RMB.
If the platform refuses to carry out the remedial actions as suggested by certification and rectification bodies, the refusal could bring criminal liabilities to the platform and its executives.
In some industries such as hoteling and logistics, CP is compulsory on a de facto basis. CP certification is a prerequisite condition to obtain the business license in the industry of hoteling and logistics.
Where is the place to store data?
According to CSL, CIIO must store its personal identifiable information (“PII”) and important data in nowhere but China. CSL does not provide such requests to non-CIIOs. However, in order to get certified under CP, a company has to store its data or have a copy of the data in China. In practice, there could be some leeway, which mostly depends on how necessary the data will have to be transferred and stored outside China.
Case #4:
A global hotel group consisting of tens of thousands of hotels will have to centralize the management of data in the headquarters that is not located in China. The concerned certification body still gives green light to the CP certification of the hotels that are located in China. However, a company that is certified by the same certification body (and rectified by us) was requested to take back their data from the server located outside China – the reason is simple – the company does not have to transfer and store its data outside China.
Therefore, a multinational company will have to manage well how and where to collect and store its data in order to get certified for classified protection under China’s Cybersecurity Law. What is more important, a multinational company should seriously consider getting classified protection to have its network vulnerabilities checked and plugged up. As such, the company could reduce the risk exposure and liabilities (which could be both administrative and criminal) under Cybersecurity Law and the Criminal Law.
Does a traditional manufacturer need to do CP?
The answer is yes. CP has evolved into Version 2, which provides for generic requirements as well as extended requirements for cloud computing system, mobile interconnection system, Internet of Things, big data and industrial control system. Because a traditional manufacturer has industrial control system, the system has to get certified for CP as well.

Case #5
A factory of a nation installed 3000 separators to concentrate the fuel of nuclear reactor by rotating at supersonic speed. If these 3000 separators are put into operation, it will be an important step towards the manufacture of nuclear weapons. A superpower state, in order to disrupt the plant's plan to produce enriched nuclear reactor fuel, hacked into the plant's industrial control system and successfully reduced the speed of the separators, thus successfully delaying the plant's plan to produce enriched nuclear reactor fuel.
In short, classified protection is a very important risk management tool for the purpose of managing some compliance risks under China’s Cybersecurity Law. With the system of classified protection established, an entity could effectively fend off some coherent cyber risks and make a golden shield to protect the entity and its executives.
_________
The author, Henry Chen, licensed to practice law in China and New York, is a senior partner at the Dentons office in Shanghai. Before joining Dentons, Henry was AP Compliance Director of Ford. Henry Chen is also Certified Information Security Personnel (CISP) and Critical Information Infrastructure Personnel (CIIP).

Henry Chen is a drafter of China national standard (draft) Information security technology-Cyber-data process security specification (信息安全技术 网络数据处理安全规范) and some other standards.
Henry's practice areas include cyber security and data governance, FCPA, anti-bribery and fraud investigations, economic sanctions and trade controls, compliance management systems, corporate matters and dispute resolution. You can reach Henry by sending an email to henry.chen@dentons.cn. Henry is the author of the book Risk Management on Commercial Bribery in China and the book Compliance Risks of Enterprises in Globalization: Outbreak and Control.